| Package Data | |
|---|---|
| Maintainer Username: | pktharindu |
| Maintainer Contact: | pktharindu@outlook.com (P. K. Tharindu) |
| Package Create Date: | 2019-03-23 |
| Package Last Update: | 2026-02-07 |
| Home Page: | https://www.pktharindu.com/projects/nova-permissions |
| Language: | PHP |
| License: | MIT |
| Last Refreshed: | 2026-02-27 03:12:13 |
| Package Statistics | |
|---|---|
| Total Downloads: | 376,015 |
| Monthly Downloads: | 8,389 |
| Daily Downloads: | 328 |
| Total Stars: | 136 |
| Total Watchers: | 3 |
| Total Forks: | 21 |
| Total Open Issues: | 1 |


Add Permissions based authorization for your Nova installation via Role-Based Access Control (RBAC). Roles are defined in the database whereas Permissions are defined in the code base. It allows you to group your Permissions into Groups and attach it to Users.
If you like this package, show some love by starring the repo. 🙏
This package is inspired by Silvanite\Brandenburg as it has clear separation of concerns.
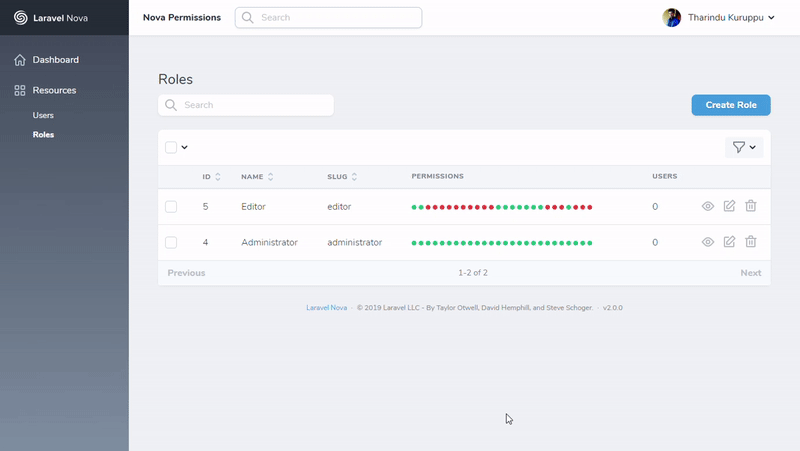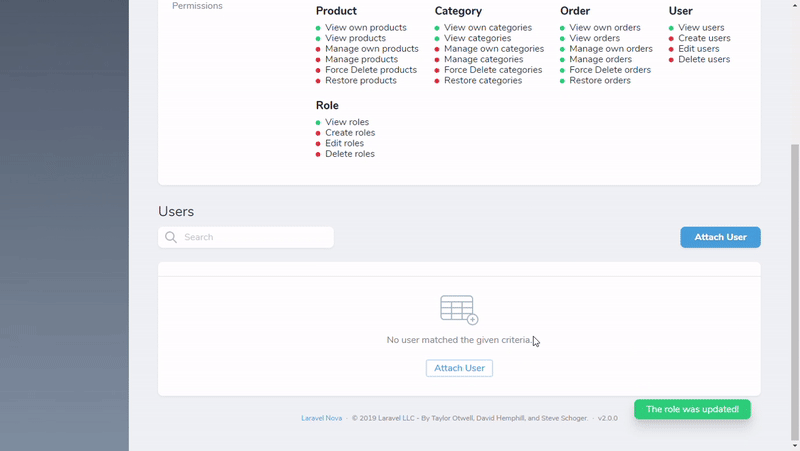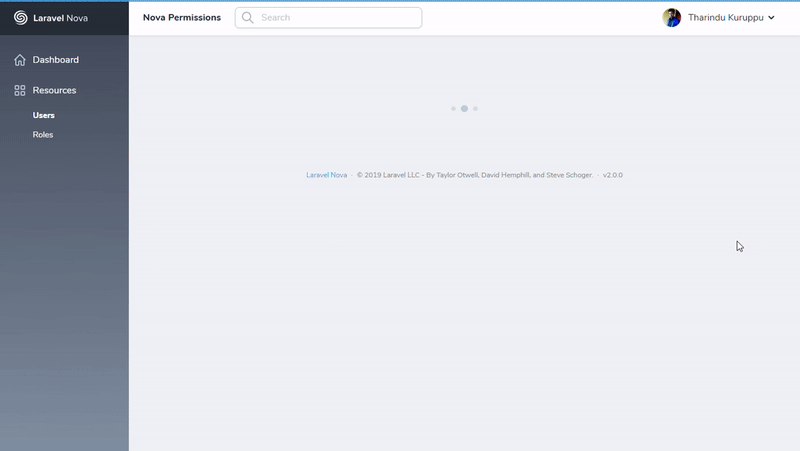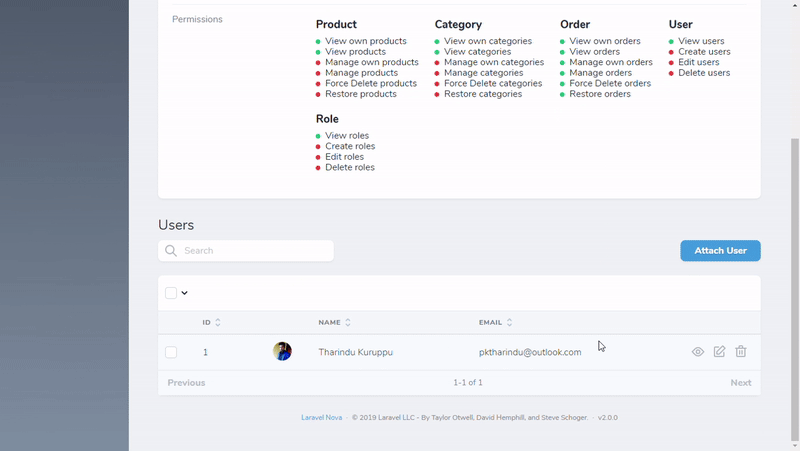
Roles are defined in the Database
and
Permissions are defined in the Codebase
As a result, you won't see any Permissions resource. The Roles resource will get the permissions from the Gates defined in your code.
You can install the package in to a Laravel app that uses Nova via composer:
composer require pktharindu/nova-permissions
Publish the Configuration with the following command:
php artisan vendor:publish --provider="Pktharindu\NovaPermissions\ToolServiceProvider" --tag="config"
Configuration file includes some dummy permissions for your refference. Feel free to remove them and add your own permissions.
// in config/nova-permissions.php
<?php
return [
/*
|--------------------------------------------------------------------------
| User model class
|--------------------------------------------------------------------------
*/
'user_model' => 'App\User',
/*
|--------------------------------------------------------------------------
| Nova User resource tool class
|--------------------------------------------------------------------------
*/
'user_resource' => 'App\Nova\User',
/*
|--------------------------------------------------------------------------
| The group associated with the resource
|--------------------------------------------------------------------------
*/
'role_resource_group' => 'Other',
/*
|--------------------------------------------------------------------------
| Database table names
|--------------------------------------------------------------------------
| When using the "HasRoles" trait from this package, we need to know which
| table should be used to retrieve your roles. We have chosen a basic
| default value but you may easily change it to any table you like.
*/
'table_names' => [
'roles' => 'roles',
'role_permission' => 'role_permission',
'role_user' => 'role_user',
'users' => 'users',
],
/*
|--------------------------------------------------------------------------
| Application Permissions
|--------------------------------------------------------------------------
*/
'permissions' => [
'view users' => [
'display_name' => 'View users',
'description' => 'Can view users',
'group' => 'User',
],
'create users' => [
'display_name' => 'Create users',
'description' => 'Can create users',
'group' => 'User',
],
// ...
],
];
Publish the Migration with the following command:
php artisan vendor:publish --provider="Pktharindu\NovaPermissions\ToolServiceProvider" --tag="migrations"
Migrate the Database:
php artisan migrate
Next up, you must register the tool with Nova. This is typically done in the tools method of the NovaServiceProvider.
// in app/Providers/NovaServiceProvider.php
public function tools()
{
return [
// ...
new \Pktharindu\NovaPermissions\NovaPermissions(),
];
}
Create a new policy:
php artisan make:policy RolePolicy --model=\Pktharindu\NovaPermissions\Role
After that, register the RolePolicy along with any other policies you may have and define the gates in the boot method of the AuthServiceProvider like below.
// in app/Providers/AuthServiceProvider.php
use Illuminate\Support\Facades\Gate;
use Pktharindu\NovaPermissions\Traits\ValidatesPermissions;
use Illuminate\Foundation\Support\Providers\AuthServiceProvider as ServiceProvider;
class AuthServiceProvider extends ServiceProvider
{
use ValidatesPermissions;
protected $policies = [
\Pktharindu\NovaPermissions\Role::class => \App\Policies\RolePolicy::class,
];
public function boot()
{
$this->registerPolicies();
foreach (config('nova-permissions.permissions') as $key => $permissions) {
Gate::define($key, function (User $user) use ($key) {
if ($this->nobodyHasAccess($key)) {
return true;
}
return $user->hasPermissionTo($key);
});
}
}
}
Then, use HasRoles Traits in your User model.
// in app/User.php
use Illuminate\Notifications\Notifiable;
use Pktharindu\NovaPermissions\Traits\HasRoles;
use Illuminate\Foundation\Auth\User as Authenticatable;
class User extends Authenticatable
{
use HasRoles,
Notifiable;
// ...
}
Finally, add BelongsToMany fields to you app/Nova/User resource:
use Laravel\Nova\Fields\BelongsToMany;
public function fields(Request $request)
{
return [
// ...
BelongsToMany::make('Roles', 'roles', \Pktharindu\NovaPermissions\Nova\Role::class),
];
}
A new resource called Roles will appear in your Nova app after installing this package.
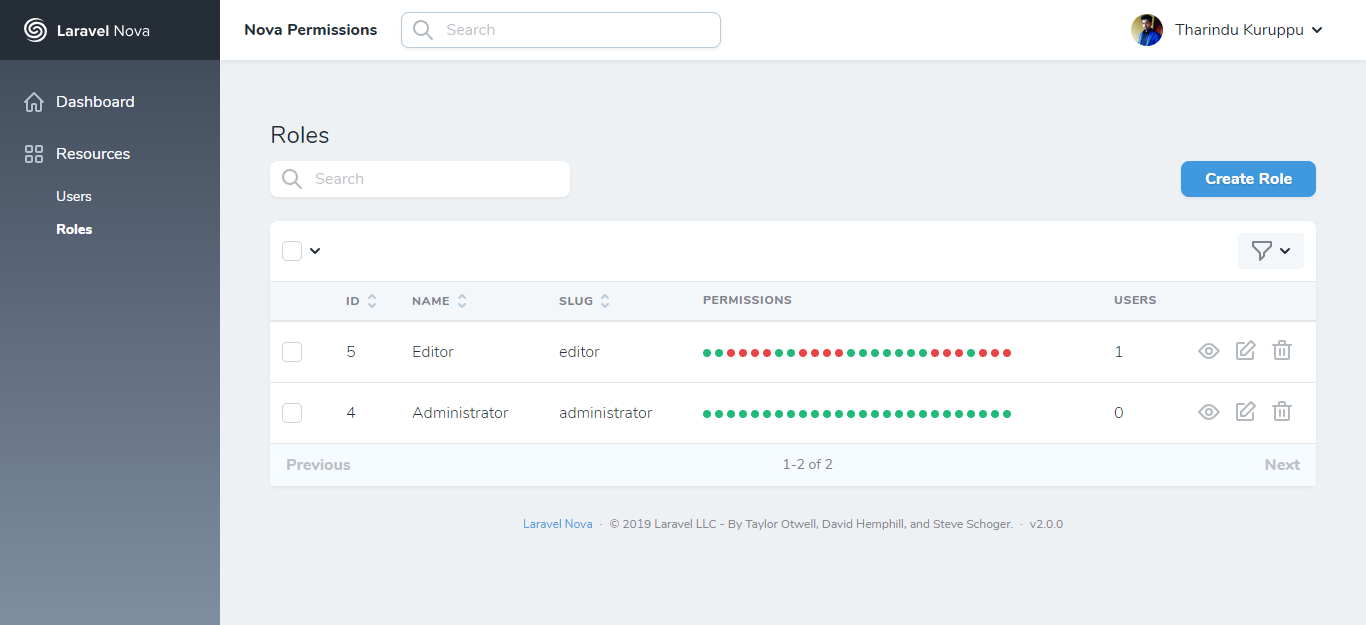
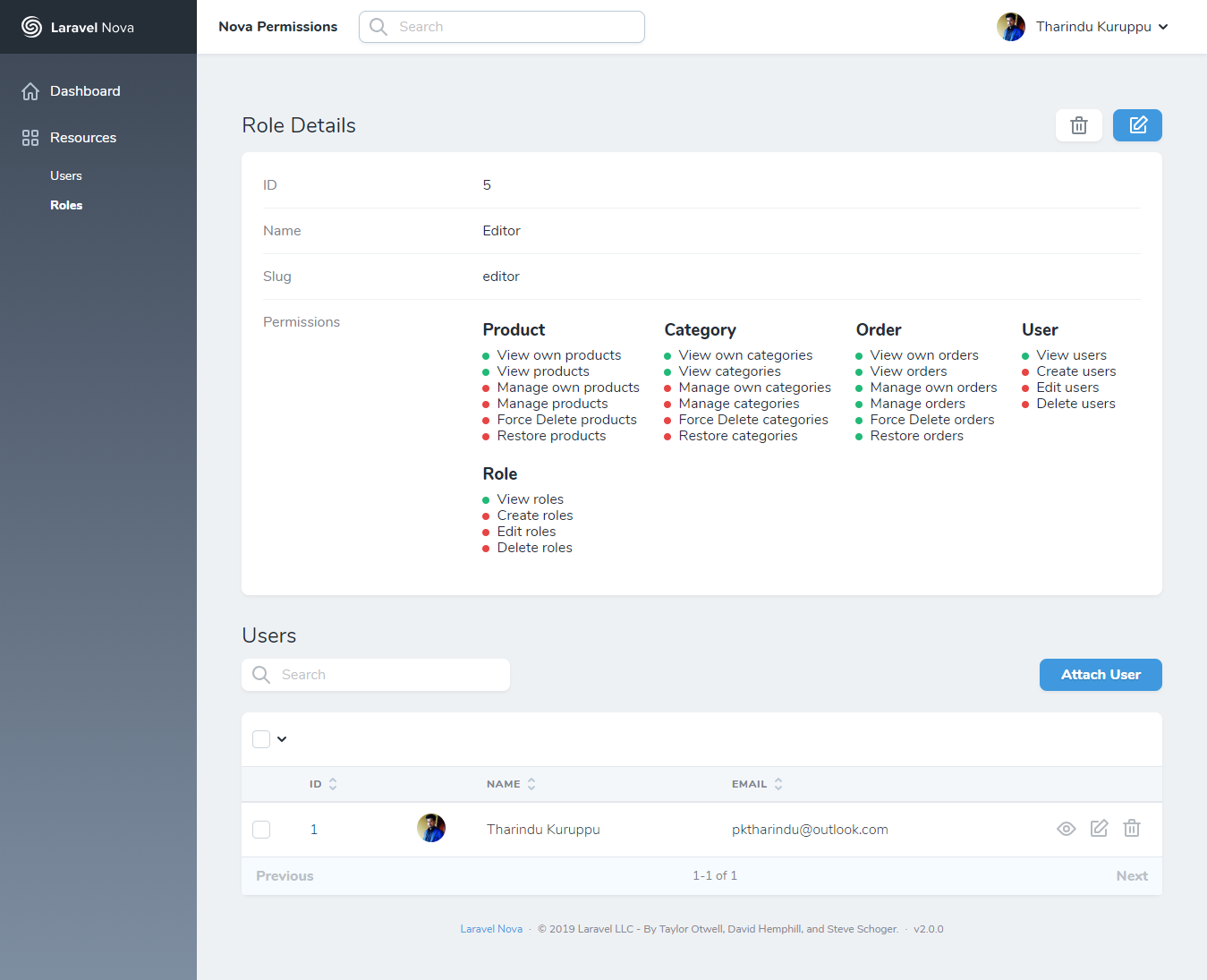
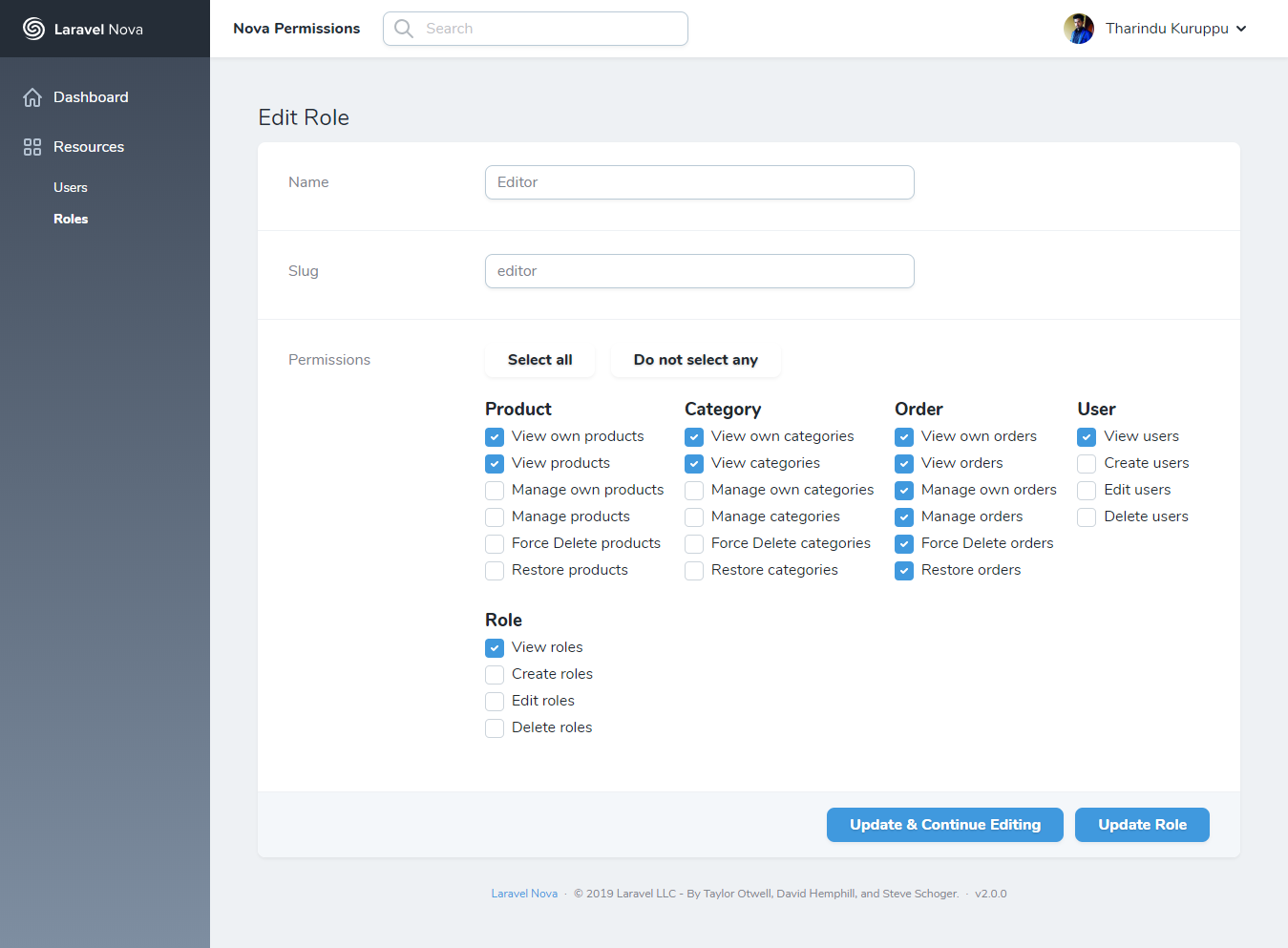
To check permissions, you can create Model Policies that works with Laravel Nova.
Note: This package doesn't come with any
Model Policiesbuilt-in. The dummy permissions defined in the config are for your reference only. For eachNova Resourceincluding theRoleandUserresources, that you want to authorize user actions against, you need to create a Model Policy. Please refer to the Laravel Docs and Laravel Nova Docs for additional information.
For Example: Create a new Post Policy with php artisan make:policy PostPolicy with the following code:
<?php
namespace App\Policies;
use App\Post;
use App\User;
use Illuminate\Auth\Access\HandlesAuthorization;
class PostPolicy
{
use HandlesAuthorization;
public function view(User $user, Post $post)
{
if ($user->hasPermissionTo('view own posts')) {
return $user->id === $post->user_id;
}
return $user->hasPermissionTo('view posts');
}
public function create(User $user)
{
return $user->hasAnyPermission(['manage posts', 'manage own posts']);
}
public function update(User $user, Post $post)
{
if ($user->hasPermissionTo('manage own posts')) {
return $user->id == $post->user_id;
}
return $user->hasPermissionTo('manage posts');
}
public function delete(User $user, Post $post)
{
if ($user->hasPermissionTo('manage own posts')) {
return $user->id === $post->user_id;
}
return $user->hasPermissionTo('manage posts');
}
}
It should now work as exptected. Just create a Role, modify its Permissions and the Policy should take care of the rest.
Note: Don't forget to add your Policy to your
$policiesinApp\Providers\AuthServiceProviderand define the permissions inconfig\nova-permissions.php.
hasPermissionTo()method determine if any of the assigned roles to this user have a specific permission.
hasAnyPermission()method determine if the model has any of the given permissions.
hasAllPermissions()method determine if the model has all of the given permissions.
view own postsis superior toview postsand allows the User to only view his own posts.
manage own postsis superior tomanage postsand allows the User to only manage his own posts.
If you want to use your own role resource, you can define it when you register the tool:
// in app/Providers/NovaServiceProvider.php
// ...
use App\Nova\Role;
public function tools()
{
return [
// ...
\Pktharindu\NovaPermissions\NovaPermissions::make()
->roleResource(Role::class),
];
}
Then extend the Pktharindu\NovaPermissions\Nova\Role in your role resource:
// in app/Nova/Role.php
use Pktharindu\NovaPermissions\Nova\Role as RoleResource;
class Role extends RoleResource
{
// ...
}
If you require any support please contact me on Twitter or open an issue on this repository.
This Package is inspired by eminiarts/nova-permissions and silvanite/novatoolpermissions. I wanted to have a combination of both. Thanks to both authors.
Copyright © 2018-2020 P. K. Tharindu and contributors
Licensed under the MIT license, see LICENSE for details.